The U2F Authenticator
If you have basic questions about Passkeys, you can find more information here: Passkeys.

U2F (Universal Second Factor) is the newest and most secure method to secure an account against password theft. Just as with the "Authenticator", a third factor is then required for the login in addition to the username (which can be changed) and password. In contrast to the "Authenticator", where you type in a 6-digit code from your smartphone, with the U2F procedure you simply connect the small USB device, e.g. the Yubikey from Yubico, to your computer and press the button on it (if the key with button is used) and you are already logged in. The U2F procedure is very easy and also extremely secure. There is no need to manually enter passwords or codes, as is the case with the "Authenticator".
We list a selection of U2F devices in the course of the help text.
Advantages of the U2F Authenticator
In addition to the general advantage of cryptographically secured two-factor authentication, the U2F method offers several other technical advantages: It protects against so-called man-in-the-middle attacks, where, for example, a criminal manipulates the connection between the browser and the mail.fr servers. This is difficult, but conceivable in certain environments. In addition, U2F protects against phishing. If an attacker lures you to a website that looks exactly like mail.fr but can be reached at https://nail.de, for example, you may not notice the trick with the wrong domain and the wrong website may receive the login data you willingly entered. This cannot happen with U2F, because U2F also checks the correctness of the domain, so that only the domain https://mail.fr receives the U2F login data for access to the mail.fr mailbox.
Important information about the U2F Authenticator
The U2F Authenticator is a small USB device, such as a USB stick. As with all technical devices, it can stop working overtime or get lost. Therefore, we recommend configuring the "Authenticator" in addition to the U2F Authenticator to have a backup for the login. Or you can maintain two U2F devices and keep one of them securely in a lockable cabinet and carry the second device with you for regular use, for example on your key ring. If the device on your keychain breaks, you can fall back on the second U2F key securely stored in the cabinet.
Most U2F authenticators are connected to the computer via USB. If you want to log on to a computer that does not have an accessible USB socket, the new U2F procedure cannot be used. This also applies to smartphones and tablets. Nowadays, there are already U2F devices that can connect wirelessly to the computer/smartphone via Bluetooth or NFC (near-field communication), but these U2F authenticators are more expensive. Here, too, it may be a good idea to use both authenticator methods and to use one or the other depending on which computer you are currently logging in to. However, the U2F method is preferable.
Example U2F devices
In general, our service supports any U2F-capable device. Below we list some of the current devices that are available for order (as of 2016):
- Almost all Yubikeys from Yubico are U2F-capable (USB-A, USB-C, NFC)
- Happlink/Plug-up Security Key
- Neowave Keydo or Neowave Winkeo-A FIDO2
- HyperFIDO Mini Pro
U2F Authenticator will soon be available for purchase directly from us




Set up U2F Authenticator
To add a (further) U2F Authenticator to the e-mail account:
-
Click on "Account/Customer data/U2F Authenticator" in the settings mode.
-
Click on the button "Register U2F Authenticator".
-
In the next step, please insert your U2F Authenticator into the USB socket.
-
Press the button on it, if you are using a U2F Authenticator with a button. The device will now be added to the list of devices and the U2F Authenticator is ready to be set up.
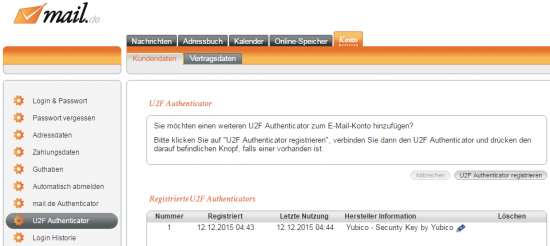
-
The next time you log in to the webmailer, after entering your username and password, you will also be asked to use the U2F Authenticator.
-
You will only be successfully logged into the e-mail account if all 3 pieces of information (username, password and U2F Authenticator) are correct.

U2F on a Linux computer
Under Linux, the browser (Google Chrome) first of all has no access to USB devices. If the U2F registration process or login does not work, it is probably due to this rights' problem.
The following procedure solves the problem:
- A file /etc/udev/rules.d/70-u2f.rules must be created with the content from the following link: https://github.com/Yubico/libu2f-host/blob/master/70-u2f.rules
- After saving, restart the system.
Google Chrome should then recognise the U2F device and have access to it.
